During the bustling online shopping period of Thanksgiving weekend, while revenue-focused teams basked in the surge of sales, threats lurked amidst the swelling tide of online traffic. To gain a broader understanding of the threat landscape during this period, we analyzed attack activities during the “Cyber 5” weekend – the five-day period between Thanksgiving and Cyber Monday – with a particular focus on commerce sites. We examined how consumer behavior intersects with attack activities to identify prevalent threats and highlight the nuanced dynamics of security risks amidst the busiest shopping days of the year.
Key Insights from our analysis:
Black Friday Leads the Charge: Black Friday stood out with a significant spike in CDN traffic, experiencing a week-over-week increase of more than 10% and peak-period surges of over 50%.
Web attacks in focus: Reflecting on year-over-year data against our top 100 commerce companies, the data revealed a 60% increase in attacks, with a significant shift in attack distribution from Thursday in 2022 to Sunday in 2023.
Anonymous IP traffic: Approximately 80% of attack traffic originated from anonymous IP addresses, including those from TOR networks, proxies, VPNs, relays, or a connection via a hosting provider.
Layer 7 DDoS Patterns: There was a notable uptick in Layer 7 Distributed Denial of Service (DDoS) events across the weekend, with especially sharp increases on Black Friday and Cyber Monday.
Black Friday Leads the Charge
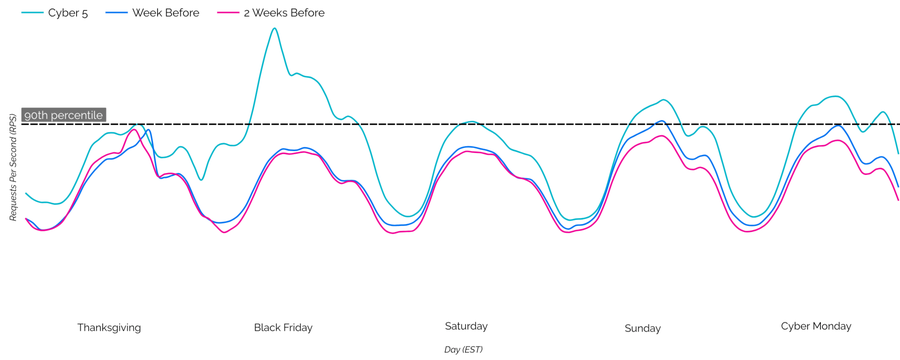
The trend of companies presenting their deals weeks ahead of Cyber 5 challenged the premise that we wouldn’t see the traditional surge in traffic over the shopping period. The uncertainty was quickly resolved, as we saw an average increase in traffic of 10% when compared to the previous weeks. Notably, Black Friday saw a surge of more than 50% of CDN traffic during peak periods – more than any other day during the Cyber 5 period. While Cyber Monday saw heightened traffic, it did not significantly distinguish itself from the overall traffic observed.
Web Attacks in Focus
Leveraging the signal data from our Next-Gen WAF (NGWAF), our analysis showed an average increase of 20% in web attack attempts compared to the previous weeks. Interestingly, the most significant surge in attacks did not happen on Black Friday or Cyber Monday, but rather from Saturday through Sunday, with as much as 90% more during peak periods, as shown in Figure 2.

Looking closer at the week of Cyber 5, we identified the five most common types of web attacks during this period: Cross-Site Scripting (XSS), SQL Injection (SQLI), Traversal, Command Execution (CMDEXE), and exploits targeting the Log4j Vulnerability (LOG4J). Notably, there was a substantial number of Traversal and XSS attack attempts between Saturday and Sunday, as shown in Figure 3.

Reflecting on year-over-year data against our top 100 commerce companies, the data revealed a 60% increase in attacks, with a significant shift in attack distribution. In 2022, the peak of these attacks was experienced on Thanksgiving, but in 2023, Sunday emerged as the new peak, experiencing a 15 % increase compared to the same day the previous year.

Anonymous IP Traffic
Enriching the attack traffic using IPInfo’s privacy dataset, we revealed that approximately 80% of the attacks during the five-day period originated from anonymous IP addresses, including those from TOR networks, proxies, VPNs, relays, or a connection via a hosting provider, which could potentially be used to tunnel traffic and mask the true IP address.

Breaking down the anonymous IP traffic by Autonomous System (AS) sources shows that about 55% of the traffic originates from Digital Ocean and over 70% of attacks were within the United States.

These insights highlight the challenges in tracing and managing security threats that leverage anonymizing services to obfuscate malicious activities.
Layer 7 DDoS Patterns
Significant increases in Layer 7 DDoS events were observed on Black Friday and Cyber Monday. When compared to our NGWAF attack data, the peak periods of attack traffic observed on Saturday and Sunday do not coincide with these DDoS events. This challenges the notion that DDoS attacks are used to mask exploitation attacks.

Overall the sources of these events were very distributed, with the top Autonomous Systems (AS) sources being very evenly matched. However, the data shows a shift from the expected dominance of cheap VPS providers as the source of these DDoS events, to a more distributed mix between VPS providers and home ISPs.

This fairly even distribution cannot be said for the source country of the DDoS events, with Indonesia standing out from the top 10 at 16%. This is not surprising considering Indonesia is one of the top countries in the world for MikroTik routers, as indicated by data from Shodan.
MikroTik routers are common and are highly targeted for botnets. Attackers exploit the router’s vulnerabilities to absorb them into the botnet, then use them as proxies to hide the true source of the botnet’s traffic. MikroTik router botnets have been a common source of DDoS attacks analyzed by our Customer Security Operations Center (CSOC) team.
Recommendations
Focus on high-risk periods: Increase monitoring and consider updating WAF rules, patching known vulnerabilities, and conducting regular resilience tests and chaos experiments. For additional guidance, refer to our blog, Managed Security Tips for Black Friday.
Use rate limiting: Rate limiting helps control the spikes in traffic experienced during a DDoS attack. We also recommend using a tiered approach with rate limiting thresholds, like applying stricter thresholds to more sensitive paths, including authentication pages, search pages, and other resource-intensive endpoints.
Apply controls around Anonymous IP sources: Defenders can use the presence of Anonymous IP sources to enrich security policies on demand as a preemptive measure. Specifically, we recommend implementing more stringent controls, such as increased logging, monitoring, and threshold-based actions when these attributes are detected.



